The Hidden Crisis: Why 98% of Domains Are Flying Blind on Email Security
98% of domains lack proper email security, costing businesses billions each year. Daniel Strauß of InterNexum reveals why most are at risk – and how to fix it.

© Funtap | istockphoto.com
When we talk about digital risks, the media conversation often focuses on spectacular system vulnerabilities or large-scale cyberattacks. Yet there is another layer of security that quietly underpins almost every interaction online: the trustworthiness of domains and email communication. At my presentation during eco’s Internet Security Days (ISD) 2025, I set out to highlight this hidden crisis – why 98% of domains remain unsafely configured, how this exposes businesses to billions in losses globally, and what practical steps can close the gap.

In a time where digital transformation dominates boardroom discussions, a startling reality lurks beneath the surface: 98% of domains are unsafely configured, leaving businesses vulnerable to sophisticated cyberattacks that cause billions in global damages each year and cost the German economy hundreds of millions. If your company owns a domain, it’s probably one of them. This isn’t just another cybersecurity warning – it’s an urgent wake-up call backed by hard data and economic consequences that no business can afford to ignore.
The scale of the problem
The numbers paint a sobering picture. Globally, around 370 billion emails are sent every single day – a staggering volume that has grown from 330 billion just last year. Within this digital deluge, the vast majority of successful cyberattacks begin with a single, deceptively simple tool: a forged email or compromised domain. And every day, billions of forged emails appear to come from trusted brands – from banks to ministries.
In Germany, the latest situation report (Lagebericht - The State of IT Security in Germany) reveals equally concerning statistics:
- €206 million in cybercrime damages (2023)
- 72% of companies affected
- 2.6 million malicious attachments registered in one year
- 37% of incidents starting with phishing or phishing malware
- Just 32% clearance rate for cybercrime cases
Recent analysis of 25,000 domains across Germany’s critical infrastructure sectors reveals another shocking truth: only 6% of companies have effectively implemented the email security measures required by IT baseline protection standards. Even more concerning, a mere 25 companies out of the entire sample had properly implemented email and domain protection as mandated by current regulations.
These aren’t just statistics – they represent real vulnerabilities in systems that power everything from banking to healthcare, energy distribution to government services. When DNSSEC implementation hovers at just 5%, the foundation of digital trust becomes dangerously unstable.
The business impact: Beyond security concerns
The consequences extend far beyond cybersecurity incidents. Consider a typical mid-sized company with an email marketing list of 25,000 recipients, sending weekly campaigns. Industry studies indicate that 15% of business emails worldwide fail to reach their intended recipients, blocked by spam filters or outright rejection due to poor authentication.
This translates to 15,000 lost emails monthly for our example company. With a modest 1% conversion rate and an average cart value of €100, this represents €15,000 in lost revenue each month – €180,000 annually from a single marketing channel alone. Scale this across larger organizations or multiple campaigns, and the economic impact becomes substantial.

What makes this problem dangerous is its invisibility – most businesses don’t even realize that their legitimate emails never reach the inbox. And the hidden cost isn’t just in lost sales. It’s in damaged customer relationships when legitimate communications fail to arrive, increased customer service burden from confused recipients, and the gradual erosion of brand trust when emails consistently land in spam folders.
Understanding the authentication challenge
The complexity of email security can be understood through a familiar metaphor: airport security. Just as flying requires multiple checkpoints, secure email communication relies on three critical authentication mechanisms.
- SPF (Sender Policy Framework) – the passenger list.
Which servers are authorized to send mail on behalf of your domain? - DKIM (DomainKeys Identified Mail) – the boarding pass.
A cryptographic signature verifying the message really comes from you. - DMARC (Domain-based Message Authentication, Reporting & Conformance) – the ID check at the gate.
It links SPF and DKIM and instructs receivers how to handle failures.
Without all three working in concert, the system fails. An attacker who bypasses one checkpoint might still be stopped by another, but gaps in implementation create vulnerabilities that cybercriminals readily exploit. And yet, most domains still fail one of these checks – meaning anyone could board their flight under a false name.
The regulatory landscape
Recognition of this crisis extends to the highest levels of German cybersecurity policy. The Federal Office for Information Security (BSI) has identified email security as a critical national concern, launching the “Email Security Year 2025” together with industry organizations eco Association and Bitkom. At its core are two guidelines:
- BSI TR-03108 – Secure Email Transport
- BSI TR-03182 – Email Authentication
Under the NIS2 directive, domain and DNS management becomes classified as critical infrastructure regardless of company size. This regulatory shift acknowledges that email security isn’t just a technical concern – it’s fundamental to economic stability and national security.
Current compliance frameworks, including IT baseline protection standards and GDPR, already establish due diligence requirements for domain security. However, the implementation gap between regulatory expectations and business reality remains enormous. Those who invest in email trust now gain not only security, but a measurable edge in communication, reputation, and reach.
Advanced protection mechanisms
Beyond basic authentication, emerging technologies offer enhanced security layers. MTA-STS (Mail Transfer Agent Strict Transport Security) enforces encrypted connections for email transmission, preventing interception during transit. Its companion protocol, TLS-RPT (Transport Layer Security Reporting), provides visibility into encryption failures and potential attack attempts.
DANE (DNS-based Authentication of Named Entities) represents the gold standard of email security, enabling organizations to specify exact cryptographic keys for email server communication. However, DANE requires DNSSEC implementation – a security extension that many hosting providers still don’t support natively. This infrastructure gap leaves security-conscious organizations limited by provider capabilities. Twenty-year-old standards remain unimplemented across much of the industry, forcing companies to ask: am I working with the right partner?
The competitive advantage of security
Forward-thinking organizations are discovering that robust email authentication delivers competitive advantages beyond risk mitigation. BIMI (Brand Indicators for Message Identification) technology allows companies with proper authentication to display verified logos in recipient inboxes, creating immediate trust.
The benefits are clear:
- Better deliverability
- Higher open rates
- Stronger customer trust
- Brand protection
- Competitive advantage
This visual authentication can increase email open rates by 10-30%, directly improving marketing campaign effectiveness. More importantly, it provides recipients with confidence that emails are genuinely from the claimed sender, reducing phishing susceptibility across the customer base.
Major email providers including Google, Microsoft, and Yahoo have implemented increasingly strict sender policies. Organizations without proper authentication face declining delivery rates regardless of content quality. Email reputation is now directly tied to security implementation, making authentication a business continuity requirement rather than merely a security consideration.
The path forward
The journey from vulnerability to security follows a predictable pattern. Organizations typically begin in “blind flight” – unaware of delivery failures or spoofing attempts. Implementing DMARC reporting provides insight into which systems are sending and where spoofing occurs. From there comes optimization – systematic improvement and enforcement.
Initial findings frequently expose “shadow IT” systems – forgotten servers, abandoned marketing platforms, or third-party services that continue sending emails without proper authorization. This discovery phase, while sometimes overwhelming, provides the foundation for systematic security improvement.
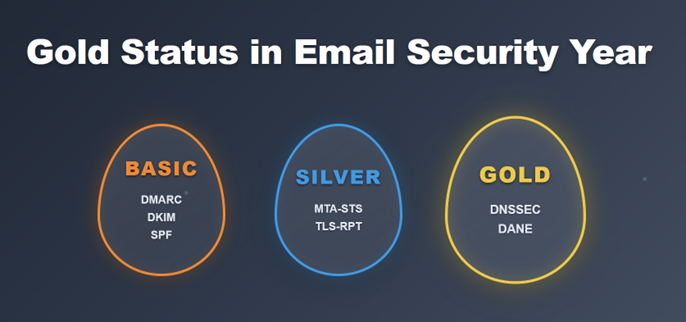
The path to comprehensive email security operates on three levels. Basic protection implements DMARC, DKIM, and SPF – the essential foundation that every organization should achieve. Silver status adds MTA-STS and TLS-RPT for transport security monitoring. And finally, gold standard implementation incorporates DANE and DNSSEC for cryptographic certainty in email communications.
To support this awareness, eco offers a free quick check at eco.domainsecurity.de, allowing organizations to evaluate their own domain’s protection level within seconds.
Taking action
The scale of this challenge might seem daunting, but the tools for assessment and improvement are readily available. The BSI provides testing resources to evaluate current security posture, while services like www.domainsecurity.info offer comprehensive domain analysis.
The critical question facing every organization isn’t whether email security matters – the economic and regulatory evidence makes this clear. The question is whether current security measures match the sophisticated threat landscape and the business’s reliance on digital communication.
As BSI President Claudia Plattner put it: “The most effective protection against phishing is when phishing emails never reach users in the first place.” That is the standard we must work toward.
The time for action is now
As cyber threats escalate and regulatory requirements tighten, organizations that proactively address email security gain sustainable competitive advantages while protecting themselves, their customers, and the broader digital ecosystem.
In an interconnected world where trust forms the foundation of digital commerce, email security isn’t just about preventing attacks – it’s about enabling business success in the digital age.
📚 Citation:
Strauß, Daniel. (October 2025). The Hidden Crisis: Why 98% of Domains Are Flying Blind on Email Security. dotmagazine. https://www.dotmagazine.online/issues/security-trust-compliance/email-domain-security-gap
Daniel Strauß is Managing Director of InterNexum GmbH and founder of nicmanager. With more than 25 years of experience in the domain industry, he is recognized as one of the leading voices in corporate domain management and email security. As a lecturer and innovator, he helps organizations and public institutions strengthen digital trust and resilience through modern domain security and risk management strategies.
Please note: The opinions expressed in articles published by dotmagazine are those of the respective authors and do not necessarily reflect the views of the publisher, eco – Association of the Internet Industry.
FAQ
Why are most domains vulnerable to email-based attacks?
According to Daniel Strauß, 98% of domains lack complete email authentication setups. Without SPF, DKIM, and DMARC, forged emails easily bypass filters, exposing businesses to phishing, fraud, and massive losses.
What are the core protocols every domain should implement?
• SPF: authorizes sending servers
• DKIM: signs emails with cryptographic proof
• DMARC: links SPF and DKIM and defines actions for failures
Together, these protect brand identity and improve deliverability.
What are the business costs of misconfigured email security?
Businesses lose revenue from blocked emails, dropped campaigns, and customer confusion. Even small errors can cause emails to land in spam, damaging trust and costing hundreds of thousands annually.
What is the difference between basic, silver, and gold email security?
• Basic: SPF, DKIM, DMARC
• Silver: adds MTA-STS and TLS-RPT for transport encryption
• Gold: includes DANE and DNSSEC for cryptographic validation
eco and BSI align these tiers with the “Email Security Year 2025” standards.
Why is DNSSEC adoption still so low?
Many hosting providers lack native support, creating technical and contractual barriers. Strauß notes this limits organizations even when they want to implement DANE, leaving gaps in the email security chain.
How does proper email security affect marketing performance?
Email authentication boosts deliverability and trust. Verified sender identity through protocols like BIMI can increase open rates by 10–30%, supporting brand reputation and reducing phishing risk.
What resources does eco provide to support domain owners?
eco offers a free email security quick check at eco.domainsecurity.de and collaborates with BSI and Bitkom to support secure implementation through campaigns, checklists, and outreach.





