Security and Trust in the Digital Ecosystems of Smartphone Apps
German smartphone apps track users three times more than global ones — and most data still flows through U.S. providers. Prof. Norbert Pohlmann & Ferhan Kesici reveal digital sovereignty risks.

@eco
Every interaction with a smartphone sets hidden digital infrastructures in motion, connecting devices to dozens of servers worldwide. An analysis of Germany’s 65 most popular apps shows that more than three-quarters of this traffic is routed through U.S.-controlled providers, concentrating control in a handful of hyperscalers. While international platforms rely on tightly integrated infrastructures, German apps depend more heavily on fragmented external services, creating greater exposure to third-party tracking and advertising. These systemic dependencies raise pressing questions of security and compliance in the digital ecosystems that millions rely on every day.
Smartphones as gateways to global infrastructure
In Germany, 69 million people own smartphones, using them as gateways to Internet services and applications. Beyond basic telephony, these devices enable email, browsing, shopping, gaming, and social media – supported by digital infrastructures that most users perceive simply as “running in the cloud.”
The Institute for Internet Security - if(is) analyzed Germany’s most widely used smartphone apps to expose how these digital infrastructures operate in practice. The investigation revealed that these 65 apps contacted more than 1,600 unique servers, with each app connecting to around 25 servers on average. WhatsApp alone serves over three billion monthly users worldwide, exemplifying the massive scale of modern mobile ecosystems. Yet each smartphone interaction activates dozens of servers across the globe, creating complex dependencies that deserve closer scrutiny.
Background
1. Digital infrastructure and sovereignty
Digital infrastructures include fiber optic cables, data centers, content delivery networks, and hyperscale cloud platforms run by providers such as Microsoft, Google, and Amazon. Digital sovereignty refers to the ability to maintain independent control over these infrastructures and the data processed within them. Key factors include:
- Geographic distribution of data centers, which affects latency, compliance, and resilience.
- Provider diversity, which reduces dependency on a few hyperscalers and strengthens operational flexibility.
2. Smartphones as endpoints
Smartphones have become universal endpoints in digital ecosystems. They initiate connections ranging from DNS lookups to encrypted and tunneled requests for messaging, banking, and social platforms. Their portability and constant connectivity enable dynamic scalability and rapid innovation, but also increase risks of dependency, privacy loss, and sustainability concerns.
3. Autonomous systems
The Internet is organized into autonomous systems (ASNs), each operated by a company. ASN assignment reflects operator policies rather than physical server locations, complicating the attribution of infrastructure control.
Methodology
Apps were drawn from the top 50 rankings of Google Play and the iOS App Store in Germany, provided by Similarweb (January 2025). After removing duplicates and unavailable apps, 65 apps remained. They were grouped as follows:
- All apps: the full set of 65.
- Top 20 apps: the most widely used, predominantly from U.S. providers.
- German apps: 14 apps from providers headquartered in Germany.
Traffic analysis was conducted using a Motorola Moto G24 running Android 14. Two methods were applied:
- On-device capture with PCAPdroid – to isolate app-specific traffic.
- WLAN port mirroring with Wireshark – to capture total traffic including background activity.
Virtual environments and root access were avoided, as many apps detect such conditions and alter behavior. Public databases (ipinfo.io, PeeringDB, GeoIP, StevenBlack) were used to classify networks and providers.
Results
Infrastructure dependencies and U.S. dominance
The 65 investigated applications from Germany’s most popular apps contacted over 1,600 servers across 6.35 autonomous systems per app on average. Amazon, Google, and Akamai dominated, with a presence in about 90% of all top apps. As Figure 1 shows, three U.S. technology giants – Google (30%), Amazon (16%), and Facebook (14%) – handled 60% of all recorded sessions. At least 75% of all top autonomous systems were U.S.-controlled.
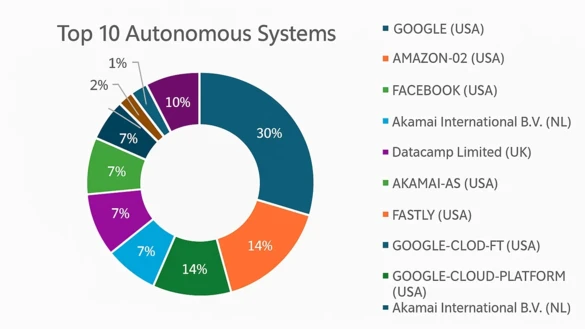
Figure 1: Distribution of Autonomous Systems in Support of all Apps (Image (if(is))
Total data volumes reached approximately 115.6 MB uploads and 2.84 GB downloads across all apps, demonstrating the substantial infrastructure demands of modern mobile applications.
Network complexity differences
German applications connected to nearly twice as many networks as international top apps (11.35 vs 5.6 ASNs), reflecting fragmented reliance on regional providers, analytics services, and CDNs (see Figure 2). International providers operated streamlined infrastructures through proprietary data centers and optimized peering agreements.
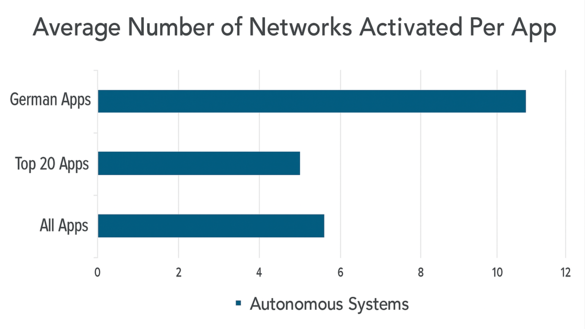
Figure 2: Average Number of Networks per App Category (Image (if(is))
Advertising and tracking analysis
DNS analysis revealed clear differences in third-party dependencies (see Figure 3). German apps generate 41% advertising and tracking traffic with 33 different tracking domains per app, compared to 15% for top international apps with 9 tracking domains per app. This suggests German apps rely more visibly on third-party tracking services, while international providers often employ less transparent server-side tracking.
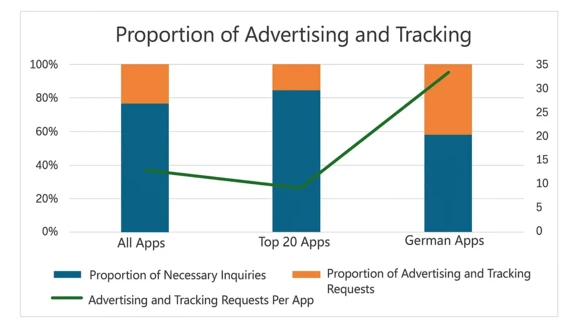
Figure 3: Ratio of Advertising and Tracking to Necessary DNS Requests (Image (if(is))
Data transfer and protocol patterns
App categories demonstrate distinct transfer characteristics. Social apps show the highest download ratios (1:32) due to media feeds, while mail apps vary significantly based on integrated services. Grocery and shopping apps maintain high download ratios (1:14 and 1:12 respectively) for product imagery and recommendations.
Despite IPv6 availability, IPv4 dominated with 96% of connections, reflecting ongoing legacy infrastructure dependencies (see Figure 4).
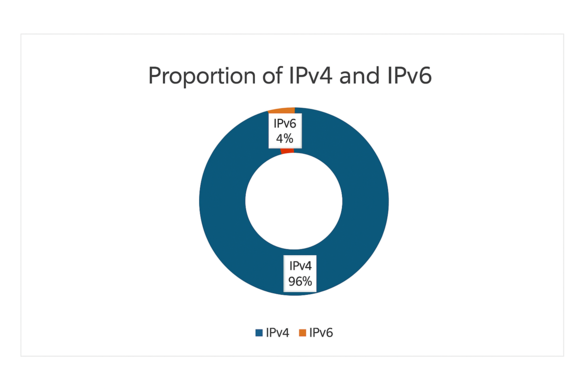
Figure 4: Comparison of the Proportion of IPv4 and IPv6 Traffic (Image (if(is))
Encouragingly, encryption was strong, with 93% of traffic secured, demonstrating positive progress in data protection measures.
Security & Trust
Two critical patterns emerge from this analysis. Firstly, U.S. hyperscalers run highly integrated infrastructures that offer efficiency and scalability, but concentrate control, creating systemic risks for security and resilience. This concentration means that technical changes, pricing decisions, or policy shifts by a few providers can impact millions of applications globally.
Secondly, German apps employ more diverse, fragmented infrastructures. While this reduces dependency on single providers, it increases operational complexity and third-party tracking exposure, potentially undermining user trust and complicating compliance with data protection regulations such as GDPR.
The high levels of encryption strengthen security posture, yet the continued reliance on IPv4 reflects lingering legacy risks and slower infrastructure modernization. The balance between efficiency and diversity remains central to achieving digital sovereignty while maintaining operational trustworthiness.
Conclusion
Smartphone applications serve as critical endpoints in global digital infrastructures dominated by a handful of U.S. providers. German apps demonstrate more distributed architectures that increase provider diversity but also operational complexity and visible third-party dependencies, creating significant implications for compliance and data protection.
Enhancing digital sovereignty requires nuanced approaches that promote infrastructure diversity while maintaining operational efficiency and user trust. European strategy should focus on developing viable alternatives to hyperscale providers, encouraging architectures that minimize unnecessary third-party dependencies, and establishing transparency standards that enable informed decision-making about data flows and security risks.
Future research should examine advertising and tracking mechanisms in greater detail, assess environmental impacts of different infrastructure approaches, and identify optimization strategies that support both sovereignty objectives and technical efficiency. The findings underscore the urgent need for policy frameworks that address the concentration of digital infrastructure control while supporting innovation and user experience.
Investment in European cloud infrastructure capabilities, combined with architectural best practices that reduce fragmentation, represents a path toward greater digital independence without sacrificing the security, performance, and compliance standards that modern applications demand.
Research conducted by the Institute for Internet Security (if(is)) at the Westphalian University of Applied Sciences.
📚 Citation:
Pohlmann, Norbert, & Kesici, Ferhan. (September 2025). Security and Trust in the Digital Ecosystems of Smartphone Apps. dotmagazine. https://www.dotmagazine.online/issues/security-trust-compliance/security-risks-german-apps-us-infrastructure
Norbert Pohlmann is a Professor of Computer Science in the field of cybersecurity and is Managing Director of the Institute for Internet Security - if(is) at the Westphalian University of Applied Sciences in Gelsenkirchen, Germany. He is also Chair of the Board of the German IT Security Association TeleTrusT, and Board Member for IT Security at eco – Association of the Internet Industry.
Ferhan Kesici studies for a Master’s degree in Internet Security at the Westphalian University of Applied Sciences in Gelsenkirchen, Germany, and is also engaged on the topic of “Analysis of Digital Infrastructure Usage by Smartphone Apps.”
FAQ
How dominant are U.S. providers in the infrastructure used by German smartphone apps?
According to Pohlmann & Kesici in dotmagazine, U.S. hyperscalers such as Google, Amazon, and Facebook handle about 60% of session traffic for the 65 most‑used German apps.
What are the risks associated with German apps relying on fragmented external services?
As Pohlmann & Kesici explain in dotmagazine, German apps’ dependence on many third‑party services increases exposure to:
• more tracking and advertising domains per app
• operational complexity, making security oversight harder
• compliance challenges under GDPR due to less transparent data flows.
How do German apps compare to international apps in terms of network diversity and efficiency?
German apps connect to almost double the number of autonomous systems (networks) on average than international top apps, according to Pohlmann & Kesici in dotmagazine. However, international providers use more streamlined infrastructures, reducing dependency on external providers.
What positive findings about security emerged in Pohlmann & Kesici's analysis?
• Encryption is strong: about 93% of traffic is secured.
• Despite legacy dependency, IPv6 adoption is present though IPv4 still dominates.
What does “digital sovereignty” mean in the context of this research?
Digital sovereignty here refers to the ability for Germany (and by extension Europe) to maintain control over the infrastructures and data flows used by apps. It implies reducing over‑dependence on hyperscale providers, increasing provider diversity, and improving transparency.
What policy or strategy recommendations emerge from this research?
Pohlmann & Kesici suggest:
• developing alternatives to U.S. hyperscale cloud and infrastructure providers
• adopting architectures that reduce unnecessary third‑party dependencies
• introducing transparency standards for data flows and tracking domains to improve trust and compliance.
How does the increased number of tracking/ad domains in German apps impact user privacy and compliance?
Pohlmann & Kesici's research shows German apps use more tracking domains per app than international apps, which can:
• increase visibility of data transfer to third parties
• complicate adherence to privacy regulations like GDPR
• risk undermining user trust if tracking is opaque.






