DNSSEC: Bridging the Trust Gap in the DNS Infrastructure
Trust starts with DNS. Patrick Ben Koetter of eco and sys4 AG breaks down why DNSSEC is essential for secure Internet infrastructure – and what's holding adoption back.

©BamBamImages | istockphoto.com
At the core of every Internet interaction is the Domain Name System (DNS) – but DNS, by itself, lacks built-in trust. This is where Domain Name System Security Extensions (DNSSEC) comes in: it ensures that DNS responses can be verified as authentic and untampered.
To deepen our understanding of current adoption challenges and to share findings directly with stakeholders, we at eco hosted a members-only webinar on 15 March 2025. The session offered an interactive exchange on the results of our DNSSEC survey and explored concrete steps toward broader implementation.
When your system receives a DNSSEC-verified DNS response, you can rest assured it was given by the authorized DNS server and the response has not been manipulated while it was in transit to your machine. You may safely use the given data and act upon it – for example, point your browser to your bank’s online service and log in into your account. Or, if it’s a DNS reply which could not be DNSSEC-verified, your system’s resolver will suppress the information and foil a potentially harmful action.
Logically, DNSSEC is something everyone should want – it’s about knowing and not just believing you’re communicating with the right service.
Commitment to widespread DNSSEC Adoption
At eco, our Email, Anti-Abuse, and Names & Numbers Competence Groups have long been committed to the rapid and widespread introduction and use of DNSSEC. The extensions offer numerous advantages, such as:
- enabling of further security protocols such as DANE (DNS-based Authentication of Named Entities)
- increased trust and reliability on the Internet
- protection against falsified DNS responses
- protection against DNS cache poisoning
- prevention of Man-in-the-Middle attacks
In light of this, the eco Association recently conducted a survey to determine which hurdles are currently still preventing companies from introducing and using DNSSEC across the board. The Competence Groups want to use this to find out how companies that are still hesitant can be helped.
DNSSEC Adoption: Key findings from the webinar
The webinar was hosted by Lars Steffen, eco’s Head of International, Digital Infrastructure & Resilience, and myself, as Leader of the eco Email Competence Group. Together, we reviewed findings from eco’s DNSSEC survey, conducted between August and December 2024, which garnered approximately 120 respondents.
Slide 1 of the survey showed that while overall awareness of DNSSEC is relatively high – with 70% of respondents stating they feel adequately informed – 30% are either unspecified or feel uninformed.
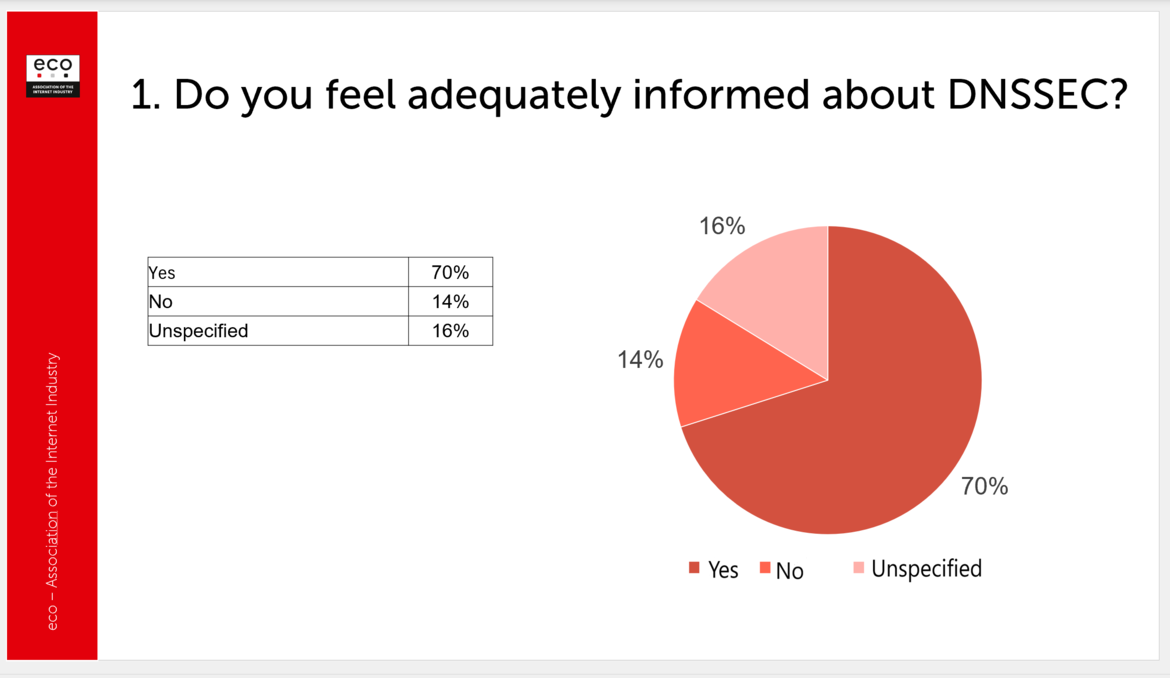
Fig. 1: Majority of respondents (70%) report feeling adequately informed about DNSSEC, according to eco Association survey data.
DNSSEC is often perceived as overly complicated. However, as I pointed out during the webinar, there have been significant improvements to simplify its implementation. I cited BIND as one example, with configuration becoming much easier compared to years ago. Additionally, an emerging initiative is underway to develop a standardized DNS administration API across popular open-source DNS services, which could further reduce complexity barriers by offering consistent interfaces regardless of the product used.
Understanding the roadblocks to adoption
As shown in the survey results, the most common reasons for not implementing DNSSEC include:
- A lack of necessary expertise (44%)
- No perceived need (16%)
- Cost-related concerns (14%)
- “Other” category (26%)
This significant “other” category led me to comment, “I don't have the crystal ball with me right now,” acknowledging that understanding these unspecified barriers would require deeper investigation in future research. Notably, there is a surprising inconsistency: although many respondents said they felt well-informed about DNSSEC, they still cited expertise as a barrier – suggesting a gap between awareness and operational confidence.
Bridging the gap between awareness and action in DNSSEC Adoption
A further central theme emerged around the disconnect between perceived awareness and actual implementation expertise. Despite many respondents indicating they feel adequately informed, a surprising number still cite lack of expertise as a barrier – prompting questions about whether the gap lies in technical knowledge or confidence in operationalizing DNSSEC. Responses show a nearly even split (approximately 50-50 when excluding unspecified responses) between those planning to introduce or expand DNSSEC and those with no plans, highlighting the persistent uncertainty in the industry.
I stressed the importance of myth-busting, hands-on education, and policy-driven adoption. DNSSEC should be the default, especially for critical infrastructure. Countries like the Netherlands, where government-backed incentives and opt-out models have driven higher adoption, contrast with Germany’s relatively stagnant uptake.
Learning from email: Industry-led momentum?
A parallel was drawn to email security protocols like SPF, DKIM, and DMARC, which only gained widespread adoption after major mailbox providers made them mandatory.
During the webinar, Mohammed Zaman from DMARC Advisor raised the question: “Do we need something like the sender requirements for DNSSEC to be more widely adopted – and is DNSSEC required to help to increase the adoption rate?” I agreed that such a push could certainly help, noting how email security protocols gained traction after major providers made them mandatory. As I further emphasized, that’s a service provider-driven view. The US government, on the other hand, requires any US office using a .gov domain to DNSSEC-enable their domain. The benefit of DNSSEC is clear – it’s just that there isn’t enough money in the market for companies to offer it.
As Slide 4 of our presentation showed, while 22% of participants use DNSSEC for over 90% of domains, many are still in early or pilot stages – or are not using it at all. This reinforces the idea that while some organizations are far along, others are only experimenting – or have abandoned it altogether.
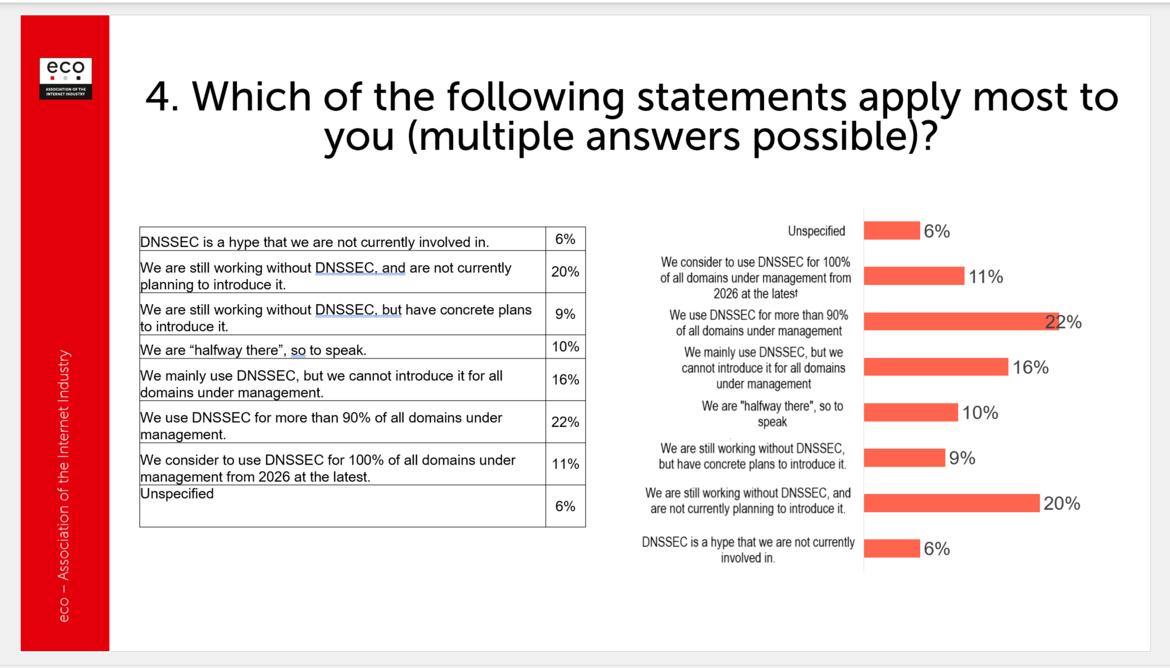
Fig. 2: Survey results on the adoption and implementation status of DNSSEC
eco plans hands-on workshop and outreach campaign
The eco Association survey results clearly indicate that the community expects the eco Association to take a more active role in promoting DNSSEC. At the webinar, Lars Steffen summarized this sentiment, noting options such as providing material, given that this is relevant for all providers based in the EU. He also highlighted that it should be promoted as the best practice. As he noted, participants called for more educational resources, implementation guidance, and technical support – especially around enabling DNSSEC in existing production environments, where uncertainty and perceived risk still deter adoption.
There is a definite need for a shift in mindset, advocating for DNSSEC to become a “comply or explain” default – particularly for critical infrastructure. There are successful efforts in countries like Switzerland, where automation through CDS/CDNSKEY has eased deployment. While some voiced skepticism about DNSSEC’s impact, the technology’s goal – trustworthy DNS communication – is more essential than ever.
In response to the feedback in the webinar, eco announced two initiatives:
- A joint awareness campaign with the German Federal Office for Information Security (BSI) to promote email and DNS security best practices.
- A hands-on DNSSEC implementation workshop for German-speaking providers in late 2025.
As was subsequently noted, participants included registries, registrars, cloud providers, email service operators, and more. This offers readers context on who participated in the survey. While diverse, the results also point to a need for better granularity in identifying respondent roles – something eco plans to refine in future surveys.
Is regulation the only way forward?
The issue is no longer technical but economic: The issues we’re having right now are issues with clashing business models. And if we don’t find business cases for the businesses, where they start earning or not spending money, they will not go and implement things. In this absence of market incentives, regulatory pressure may become necessary. The German BSI is reportedly preparing an outreach campaign in partnership with eco to promote DNSSEC and related standards across the German digital economy.
As noted by Lars Steffen: “We are working on a campaign with the BSI in Germany where we are currently preparing an outreach campaign to businesses, email service providers, hosting providers.” As he highlighted, the goal is to increase awareness around email and DNS security measures, including DNSSEC.
Final thought: No trust without verification
Our closing remarks captured the heart of the issue. Almost everything on the Internet starts by sending out a DNS query. If we can’t trust that response, then nothing built on it is reliable. DNSSEC is the only tool that is there today to verify those responses. Without it, trust remains a matter of faith – not proof.
📚 Citation:
Koetter, Patrick Ben. (2025, June 25). DNSSEC: Bridging the Trust Gap in the DNS Infrastructure. dotmagazine. https://www.dotmagazine.online/issues/strengthening-digital-trust/dnssec-bridging-the-trust-gap-in-the-dns-infrastructure
Patrick Ben Koetter is an email expert, and a board member of sys4 AG, which specializes in email, DNS, and the development of highly secure platforms and services. He contributes his knowledge and experience to eco as an expert and as Leader of the Email and Anti-Abuse Competence Groups.
Please note: The opinions expressed in Industry Insights published by dotmagazine are the author’s or interview partner’s own and do not necessarily reflect the view of the publisher, eco – Association of the Internet Industry.





