Cloud Computing Security and Privacy Framework – Ensuring Accountability for Cloud Customers and Cloud Service Providers
Linda Strick from the Cloud Security Alliance offers guidance for CSPs and cloud customers to assess the security and privacy risks of a cloud service.

© Natali_Mis | istockphoto.com
The Cloud Security Alliance (CSA) has created a control framework with fundamental security and privacy principles to guide cloud service providers and cloud customers to assess the overall security and privacy risks of a cloud service. It provides an anchor point and common language for balanced measurement of security and compliance postures and the holistic adherence to the vast and ever evolving landscape of global data privacy regulations and security standards. It addresses the inter and intra-organizational challenges of persistent information security by clearly delineating control ownership and serves as the basis for new industry standards and certifications.
The security and privacy control framework indicates a shared responsibility model determining the security obligations of a cloud service provider (CSP) and its customers to ensure accountability. It helps cloud service providers to demonstrate transparency and assurance of the cloud service, and the cloud customer can understand whether and how the security controls and practices implemented by the CSP are compliant with the security and privacy requirements.
For the community – by the community
Before moving into the cloud, a cloud customer needs to perform a risk assessment to identify restrictions and constraints that may influence the use of the potential cloud service and an external risk assessment to determine whether the CSP’s service meets the customer’s needs and compliance obligations. The CSA community, its members and experts, has created security and privacy tools that can be used for due diligence – such as the Cloud Control Matrix (CCM), Consensus Assessment Initiative questionnaire (CAIQ), Code of Conduct for GDPR Compliance and STAR Registry. The CSA CCM [1] provides a detailed controls framework that is aligned with the Cloud Security Alliance’s Security Guidance in 16 domains.
The Security Trust Assurance and Risk (STAR) program (see fig. 1) encompasses key principles of transparency, rigorous auditing, and harmonization of standards. The STAR Program presents self-assessment or third-party certification and attestation.
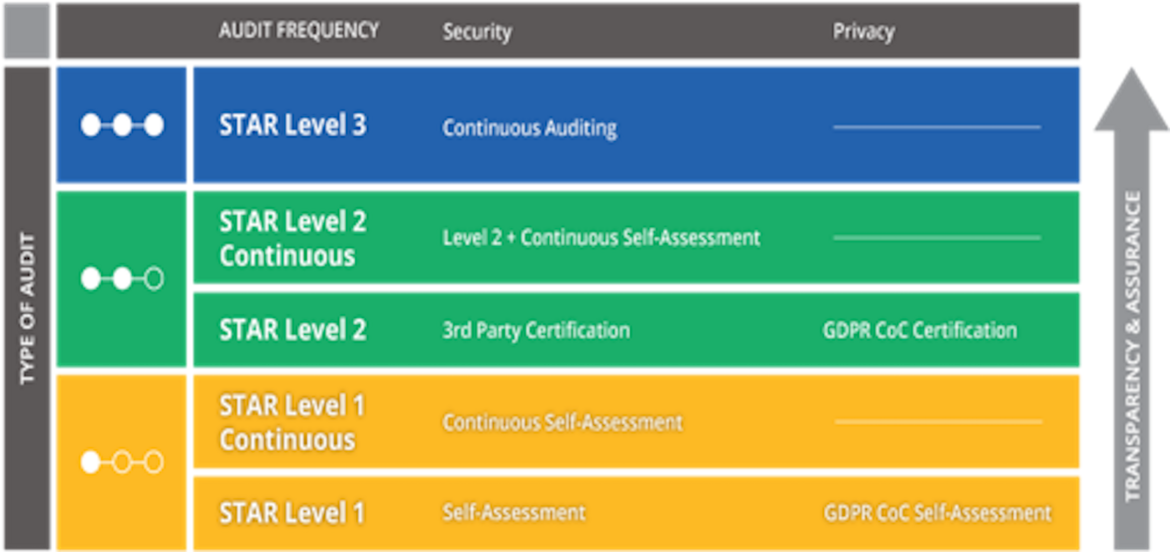
Figure 1: CSA STAR (Security, Trust and Assurance Registry), 3 Level Provider Certification Program
CCM/CAIQ helps you to identify fundamental cloud specific security objectives to better understand your risks or gaps. It outlines who is responsible for the control implementation – the cloud service provider or the customer, or both – following the shared responsibility model. It also presents an explanation of to which cloud service delivery model the control applies – IAAS, PAAS, SAAS. And it is aligned to industry standards. The cloud customer can use it to assess and compare cloud service providers and align their procurement accordingly. The Italian Government, for example, demanded that all cloud service providers in the public sector have a STAR Level 1, or perform an equivalent self-assessment.
General Data Protection Regulation Compliance and the Code of Conduct
As organizations continue their efforts to comply with Europe’s most recent regulation, CSA has also worked across the globe to provide tools like CSA STAR, for both cloud service providers and cloud customers, to ensure compliance with future regulations – alongside trust and transparency in the market. Emphasizing this aspect, CSA has a Code of Conduct (CoC) for European General Data Protection Regulation (GDPR) compliance. The CSA CoC for GDPR compliance is based on two major components, the Privacy Level Agreement Code of Practice (PLA CoP), which is a technical standard that specifies the requirements included in the GDPR, and the adherence mechanisms associated with it.
The PLA CoP specifies the application of the GDPR in the cloud environment, with the categories of requirements listed in figure 2.
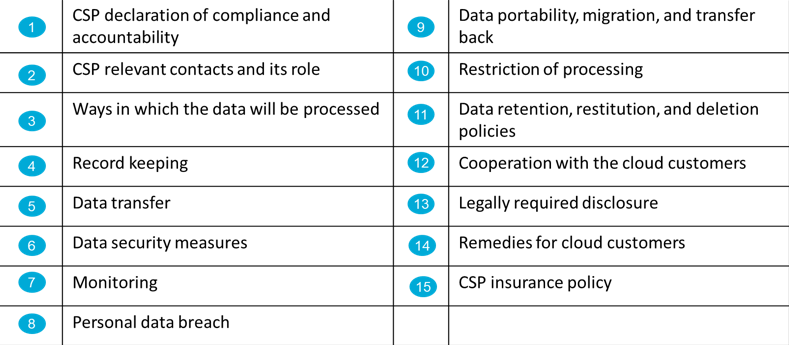
Figure 2: PLA Code of Practice requirements
Since the CSA CoC for GDPR Compliance mainly focuses on legal requirements, CSA recommends the combined adoption of this Code with other CSA best practices and certifications, such as the Cloud Control Matrix (CCM) and the STAR Certification (or STAR Attestation or STAR Self-Assessment), which provide additional guidance around technical controls and objectives for information security.
In such a context, the adoption of technical information security standards such as the Cloud Control Matrix or its equivalents [2] and the certification schemes related to them [3] will provide evidence that CSPs have implemented a security program or an information security management system (ISMS) that adequately protects consumer data from the threats outlined in these risk assessments and the Data Protection Impact Assessment.
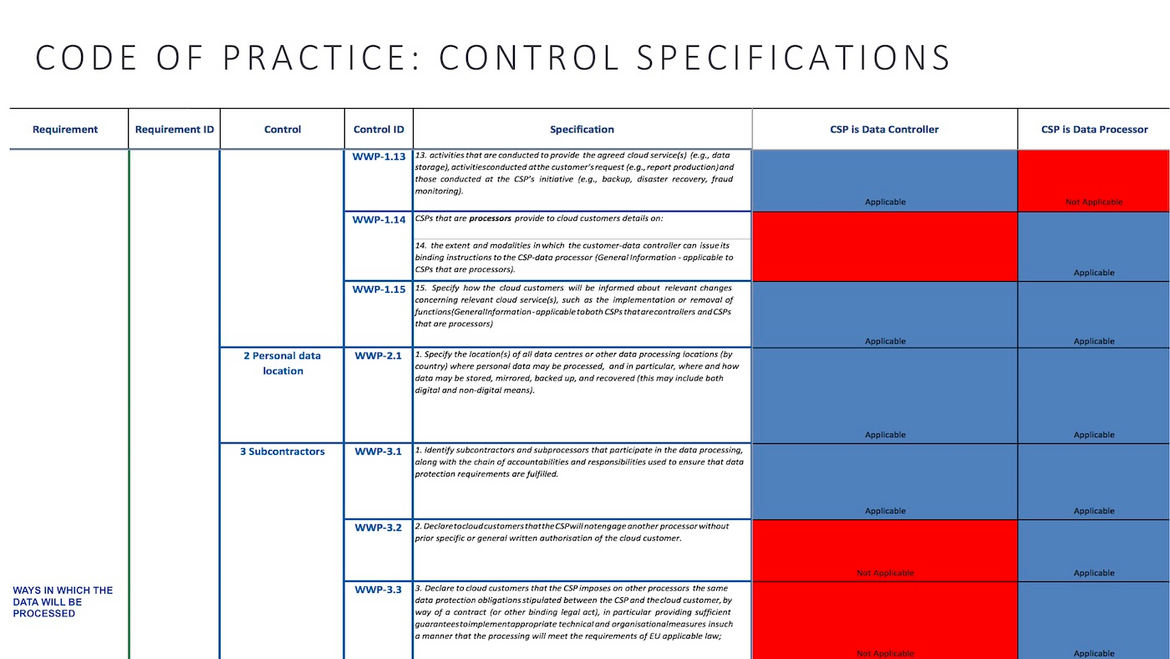
Figure 3: Code of Practice – control specification
The Privacy Level Agreement Code of Practice (PLA) reflects the GDPR requirements that are relevant in the cloud (see an example in fig 3). The CoC, through the PLA, not only seeks to promote lawful behavior on the part of adhering CSPs, but also ethical behavior. The CoC’s requirements include obligations upon CSPs which, while not strictly required by the applicable law, are necessary to guarantee a fair balance in the relationship between CSPs and cloud customers, eventually aiming to ensure that data subject rights can effectively be respected. For example: the requirement for a CSP to provide a transitional period to customers upon customer termination (as a result of an objection to a change of data processing locations or of sub-processors), during which services will continue to be provided to customers as they seek an alternative solution. This requirement seeks to prevent harm which might arise for customers, as well as for the data subjects whose data are processed by those customers, if the services provided by a CSP were abruptly ended, as a result of the customer’s exercise of their right of objection/termination.
It is worth mentioning that the terminology “Privacy Level Agreement” is used in the sense that the approach to privacy and data protection from adherents to the CoC is not a “one-size-fits-all” matter; rather, there are different levels of assurance in terms of compliance (e.g., regarding different security measures put in place, or different technical means to assist in addressing data subjects’ requests) which may be offered by adhering CSPs, which still meet the requirements of the CoC.
Moreover, it raises the bar for data protection and privacy in cloud computing by adding controls defined based on guidelines produced by the European Union Agency for Network and Information Security (ENISA), ISO standards, and additional best practices. Thus, the CoC provides a solid baseline for technical and organizational security measures to be implemented by CSPs, through the ENISA Technical Guidelines for the Implementation of Minimum Security Measures for Digital Service Providers, which allows CSPs to declare their compliance with varying levels of sophistication (1 to 3), thereby affording to CSPs the possibility to calibrate the security measures proposed by the CoC in line with their own assessment of the risks inherent to their services, in full compliance with Article 32 GDPR.
Furthermore, the CoC takes into consideration the needs of small to medium cloud providers in the scope of data protection – particularly, the need to clearly understand how the GDPR may apply to them, so that they may allocate their resources for compliance in an effective manner. Thus, the CoC provides easily understandable guidelines, also for SMEs, which may allow them to efficiently comply with applicable data protection requirements and level the playing field with larger CSPs.
Self-Assessment – CoC and STAR program
The principle of accountability is one of the leading and recurring themes across the GDPR, since at the core of the regulation there is the idea of making sure that whenever an organization is processing personal data, it must take full responsibility not only to comply with the relevant duties and obligations, but also to demonstrate such compliance. According to the principle of accountability, the organization collecting and/or processing personal data should behave as a good steward of the data during its whole lifecycle. In this regard, the idea of due diligence and control over any third-party participating in the processing of the personal data is of utmost importance.
The joint adoption of the CoC and CCM provides CSPs with a compliance suite for both legal and technical security requirements of the GDPR. The adherence to CoC and CCM requirements can be demonstrated by achieving a combination of
• STAR Certification or STAR Attestation or STAR Self-Assessment and
• CODE OF CONDUCT Self-Assessment
The STAR self-assessment can be done at no cost. You can find out how to do it here: https://cloudsecurityalliance.org/star/submit/. The Code of Conduct self-assessment can be found here: https://gdpr.cloudsecurityalliance.org/star-submit, but undertaking this involves some cost.
Despite the public discussion about self-assessment, using a tool like the CCM Questionnaire (QAIC), or CCM, to perform a self-assessment will increase your awareness of potential gaps and leads to a better understanding of your security risks. The use of the CoC enhances your accountability and minimizes the potential risk of GDPR non-compliance. It also provides cloud customers of any size with a tool to evaluate the level of personal data protection offered by different CSPs, in connection with the service(s) provided and thus supports these customers in making informed decisions. Especially for SMEs as CSPs, this is a straight-forward way to show compliance with modest costs.
References
[1] The Cloud Security Alliance’s Cloud Controls Matrix includes mappings to other industry-accepted security frameworks (such as the ISO 27001/27002, ISACA COBIT, PCI, NIST, AICPA TSP, FedRAMP and ENISA IAF). The mappings are primarily conducted by CCM Working Group volunteers or provided to CSA by third-party organizations
[2] e.g., ISO 27001 supported by ISO 27017 or 27018, or the AICPA Trust Services Criteria
[3] e.g., STAR Certification, STAR Attestation, STAR Self-Assessment, ISO 27001, or SOC2
Since August 2018, Linda Strick has been running the EMEA headquarters and the Privacy Center of Excellence of the Cloud Security Alliance in Berlin. She has been working in cloud computing, with a focus on security and privacy, interoperability/migration, and multi-cloud environments since 2010, has led several EU Horizon 2020 projects, and holds a Cloud Security Knowlege and GDPR Lead Auditor Training Certificate.
Please note: The opinions expressed in Industry Insights published by dotmagazine are the author’s own and do not reflect the view of the publisher, eco – Association of the Internet Industry.




