DDoS: From “Background Noise” to Strategic Threat
Lisa Fröhlich of Link11 warns that AI-powered DDoS attacks now threaten business continuity, reputation, and market position like never before.

© Funtap | istockphoto.com
Distributed Denial of Service (DDoS) attacks have evolved from being considered mere ‘network noise’ to a strategic threat. In early 2025, there was a 225% surge in attack numbers in the Link11 network compared to the same period in 2024. This has had a significant impact on critical infrastructure. Modern campaigns are becoming more automated, AI-driven, and politically motivated, targeting governments, companies, and digital services. Considering the challenges mentioned, it is necessary to adapt defense strategies to include adaptive, automated resilience measures. This evolution requires a re-evaluation of security policy frameworks.
DDoS attacks are no longer just digital background noise. For a long time, many companies dismissed such attacks as technical nuisances rather than serious risks. This view is now dangerously outdated. Today, DDoS attacks have become a strategic tool used by geopolitically motivated groups and professional cybercriminals alike.
The Federal Report on Cybercrime 2024, published by the German Federal Criminal Police Office (BKA), highlights this shift. More than 220 hacktivist attacks were directed against German institutions.
Within the Link11 network, the volume of attacks increased by 137% in 2024. Peak values of up to 1.4 Tbit/s were recorded. This data volume is equivalent to the simultaneous streaming of over 300,000 HD movies. Such volumes can overwhelm even robust digital infrastructures.
And the escalation continues, with Link11 recording 225% more attacks in the first half of 2025 than in the same period of the previous year.
Further development of tactics: professionalization, automation, AI-driven
The volume is not the only thing increasing. DDoS attacks are also becoming more sophisticated. Modern campaigns no longer rely solely on brute force; they use an ever-growing arsenal of methods facilitated by the following factors:
- Smarter botnets that recruit millions of IoT devices and servers worldwide.
- Professionalization of attack services, including DDoS-for-hire platforms offering turnkey campaigns on the dark web.
- Artificial intelligence is being used by attackers to dynamically adapt traffic patterns. This makes attacks more difficult to detect and defend against.
- Large-scale automation enables coordinated, multi-vector attacks that can seamlessly switch between bandwidth flooding, protocol abuse, and application-level attacks.
These developments have blurred the line between ‘noise’ and targeted disruption. DDoS attacks are now often part of long-term campaigns aimed at exhausting defenses, testing resilience, and achieving political or criminal objectives.
Attack scenarios: From Layer 7 to geopolitics
The following examples from the Link11 network demonstrate the diversity, persistence, and severity of DDoS campaigns:
1. Layer 7 paralysis: 16 million sessions per minute
A recent DDoS attack demonstrated how devastating application-level attacks can be. Within minutes, the servers were flooded with 580 million HTTP requests and experienced 16 million concurrent sessions per minute at times.
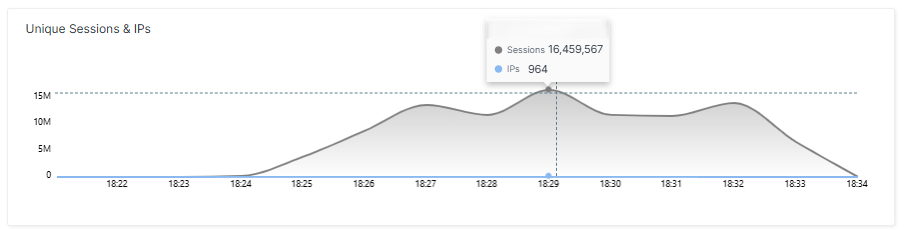
- To the outside observer, the requests appeared normal. They were simple HTTP GET calls to the root domain. There were no malformed packets or exotic protocols.
- The result: The CPU, memory, and session management on the servers collapsed, even though backbone utilization appeared stable.
- The defense systems detected the anomaly by identifying unusual request densities and abnormal access patterns. Suspicious IP ranges were blocked, but the botnet constantly switched to new sources, demonstrating learning and adaptive behavior.
This incident illustrates why Layer 7 attacks are particularly harmful: they often fall below the thresholds for volumetric detection but can paralyze applications from within.
2. Hit-and-run against an entertainment provider
Another notable case involved a digital entertainment company that was attacked nine times in the span of just six days. Unlike long-term campaigns, these were short, targeted attacks.
- Each attack lasted only five to ten minutes but peaked at a traffic rate of up to 1 Tbit/s.
- The attacks used fast ‘ramping’: the bandwidth increased from zero to several hundred Gbit/s within seconds, leaving defenders with almost no time to react.
- The attack vectors constantly changed from UDP floods to TCP bursts to rare NTP floods, making forensic analysis difficult due to the short duration and high variability.
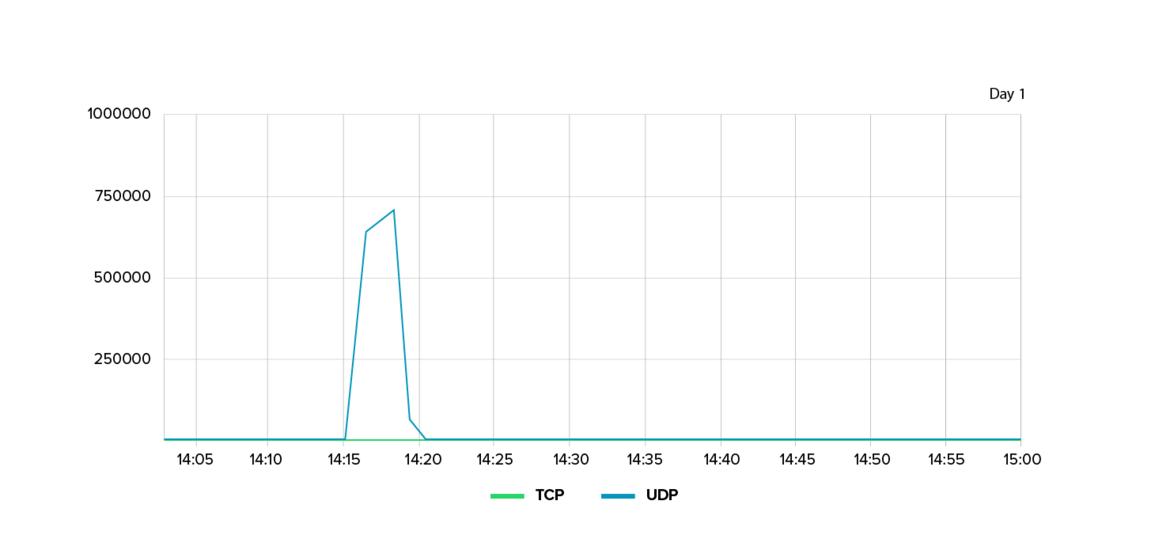
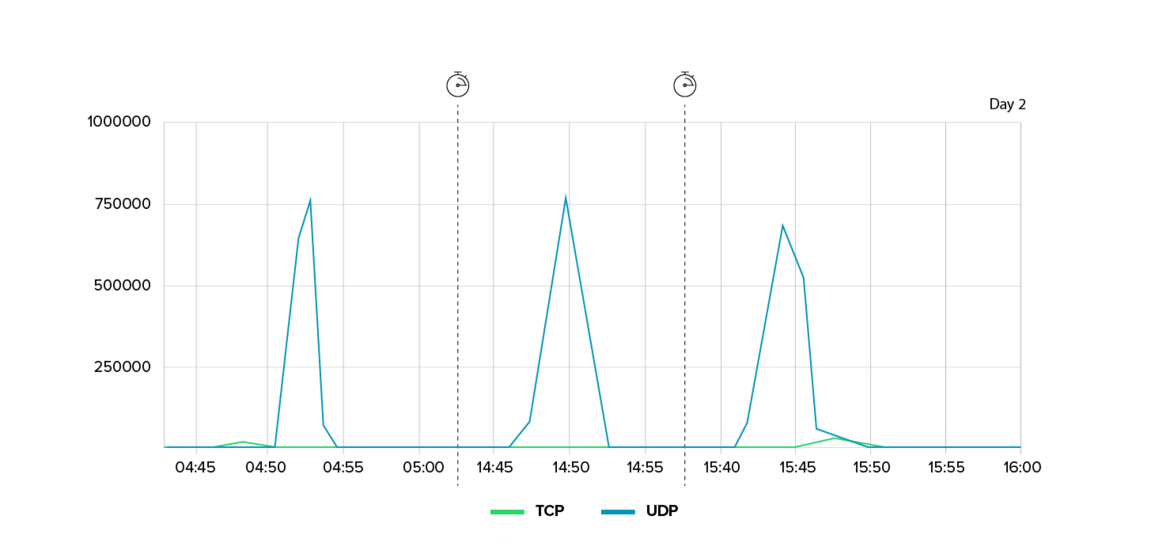
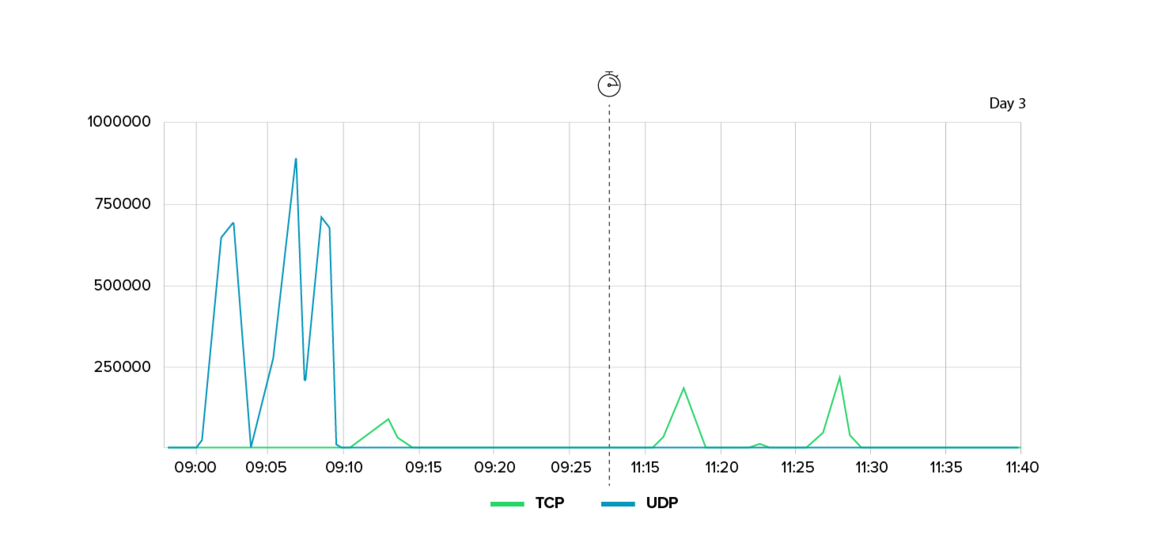
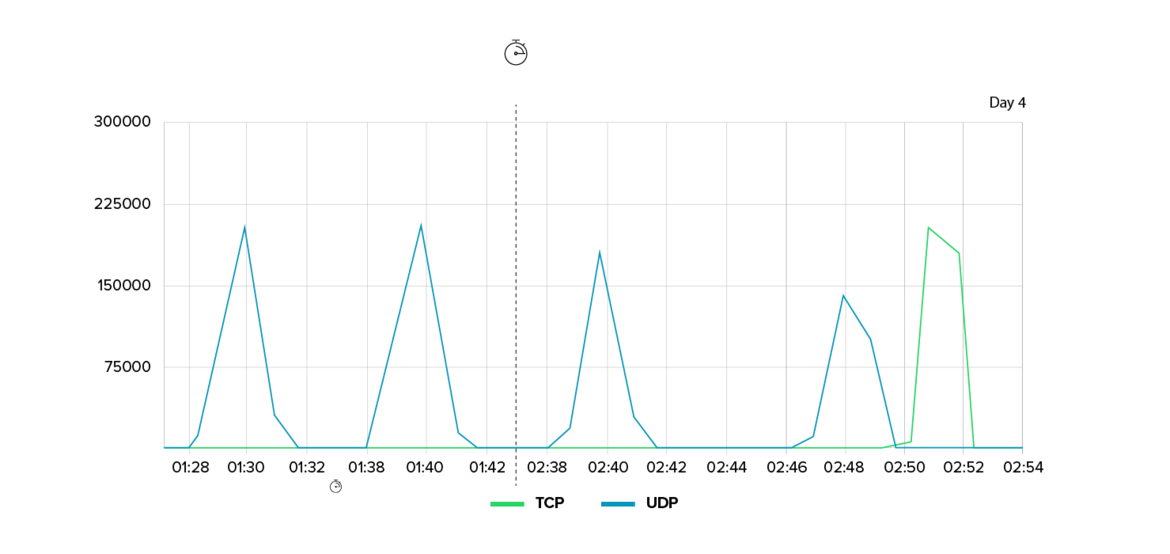
The attacks appeared to be motivated more by economics than politics, likely aimed at disrupting services, frustrating users, and undermining the company’s market position. This demonstrates how DDoS attacks are increasingly being used as competitive weapons in digital markets.
3. Geopolitical campaigns with stealth DDoS
In April 2025, amid heated debates over Germany’s planned delivery of Taurus missiles to Ukraine, the pro-Russian hacktivist group NoName057(16) escalated its digital offensive, aiming to increase visibility and cause disruption.
- City portals such as berlin.de, stuttgart.de, and nuernberg.de were unavailable for hours or even days. Disruptions also affected corporate websites, including those of Volkswagen and Commerzbank.
- A Layer 7 attack was observed amidst the noise of volumetric attacks on the Link11 network: structured HTTP requests routed through legitimate VPN and CDN infrastructures.
- By using ranges from popular VPN providers, the attackers masked the traffic so effectively that it was almost indistinguishable from genuine user access.
NoName claimed responsibility for the attacks on Telegram, amplifying their political impact by framing them as part of a larger geopolitical conflict. This case demonstrates that DDoS attacks pose not only a technical risk but also serve as a propaganda tool.
More than a technical challenge
DDoS attacks are now part of a broader cyber threat landscape. According to IBM’s X-Force Threat Intelligence Index 2025, 70% of observed cyberattacks in 2024 targeted critical infrastructure. PwC’s Global Digital Trust Insights report from 2025 highlights a concerning trend: only 2% of companies have true enterprise-wide cyber resilience, despite the fact that the average cost of a security breach exceeds $3.3 million.
The World Economic Forum’s Global Cybersecurity Outlook 2025 also warns of the emergence of crime-as-a-service, which are increasingly sophisticated, AI-driven attack platforms that lower the barriers to entry for organized cybercrime.
From defense to resilience
Despite mounting evidence, many companies continue to lull themselves into a false sense of security. However, the speed, volume, and sophistication of DDoS attacks mean that traditional manual defenses are no longer sufficient.
What is needed now:
- Adaptive defenses: Only automated, AI-powered protections can keep up with today’s fast-moving attacks.
- Resilience strategies: Companies must ensure rapid recovery and minimize damage to their reputation and operations beyond prevention.
- Political perspective: In the context of critical infrastructure and digital sovereignty, DDoS attacks must be treated as a security policy priority, not just an IT problem.
Conclusion
DDoS is now more than just traffic. Due to record-breaking volumes, politically motivated campaigns, and professionalized attack networks, DDoS has become a strategic threat requiring a fundamental change in technological defenses and corporate security culture.
📚 Citation:
Fröhlich, Lisa. (October 2025). DDoS: From “Background Noise” to Strategic Threat. dotmagazine. https://www.dotmagazine.online/issues/security-trust-compliance/ddos-from-background-noise-to-strategic-threat
Experienced communications expert Lisa Fröhlich joined the Link11 team in May 2022. In addition to traditional PR topics and content management, she is responsible for corporate communications as the company’s spokesperson. In late 2023, she launched Link11’s IT security podcast “Follow the White Rabbit.” She gained extensive experience in the field of cybersecurity as a consultant for scientific communication at the Technical University of Darmstadt. Prior to that, she worked for over a decade as a PR Manager and Press Officer in the financial sector.
Please note: The opinions expressed in articles published by dotmagazine are those of the respective authors and do not necessarily reflect the views of the publisher, eco – Association of the Internet Industry.
FAQ
How have DDoS attacks changed in recent years?
• DDoS attacks have evolved from simple bandwidth floods into complex, AI-driven operations.
• They now use smart botnets, automation, and shifting tactics to overwhelm digital infrastructure, often for political or economic reasons.
Why are Layer 7 attacks particularly dangerous?
• These application-level attacks mimic normal traffic, making them hard to detect.
• Link11 recorded 16 million sessions per minute in a Layer 7 event, paralyzing services without triggering volumetric alarms.
What are ‘hit-and-run’ DDoS attacks and why are they effective?
• Short, intense attacks that ramp up quickly and vanish before defenses respond.
• Their variability and brevity complicate detection and forensic analysis.
How are geopolitical events influencing DDoS campaigns?
• Groups like NoName057(16) target governments and corporations during political tensions.
• Lisa Fröhlich, Link11, noted disruptions to city portals and major brands in Germany in April 2025 amid arms delivery debates.
What makes AI-powered DDoS threats more serious than past attacks?
• AI adapts traffic patterns and switches sources in real time, defeating static rules.
• This requires defenders to implement automated, learning-based protections.
What does Lisa Fröhlich of Link11 recommend for modern DDoS defense?
• Shift to AI-powered, adaptive protections
• Develop resilience plans for fast recovery
• Recognize DDoS as a strategic security risk, not a technical footnote
Why must DDoS be seen as a security policy issue, not just an IT concern?
• Attacks on critical infrastructure impact national security and digital sovereignty.
• This elevates DDoS to a matter requiring cross-sector and policy-level responses, as highlighted by eco – Association of the Internet Industry.





