Shaping the Digital Production Age
Rudolf Preuss, CEO of Arendar IT-Security Ltd., explains how cybercrime is challenging today’s manufacturing landscape and how to protect industrial production from attacks.

© metamorworks | istockphoto.com
Covid-19, network consumption and cybercrime
Due to the special circumstances of the Covid-19 pandemic and the increasing number of people working from home, “broadband providers are experiencing a traffic surge between 30% and 50% across their mobile and fixed networks,” the Forbes magazine announced in March 2020. But not only network consumption is increasing.
Covid-19 is not only threatening the health of billions of humans; it is also a threat to company’s cyber-security and that of their employees. There are various causes for this. Firstly, home networks tend to be not as secured as the office IT infrastructure. Secondly, private and business usage often become mixed up within the same network. Additionally, unsecured voice-driven services can potentially record confidential conversations. But mostly, working remotely often makes it necessary to exchange confidential data in digital form. All these situations provide greater scope for hacks and attacks on the company infrastructure.
At least 68% of German industrial enterprises have been impacted by cybercrime within the last two years. This entails data theft, industrial espionage, and sabotage, with damage totalling 43.3 billion Euro. The focus of cyber criminals is still set on small to medium-sized companies (SMEs), as the study* “Espionage, sabotage and data theft – economic protection for the industry” by the German association bitkom found.
This shows why creating a secure, reliable digital infrastructure is the only answer to securing production from malware and still staying competitive – especially in the long term.

Source: ARENDAR IT-Security GmbH
Most of the time, the problem for companies does not even begin at the IT (Information Technology) level – speaking of a company’s offices – but instead at the OT (Operation Technology) level – a company’s production plants.
As Figure 1 illustrates, the standard solution available on the market is to protect both the office network and the process network by interposing a firewall. The function of a firewall is to filter which ports and protocols are to be activated and thus able to communicate.
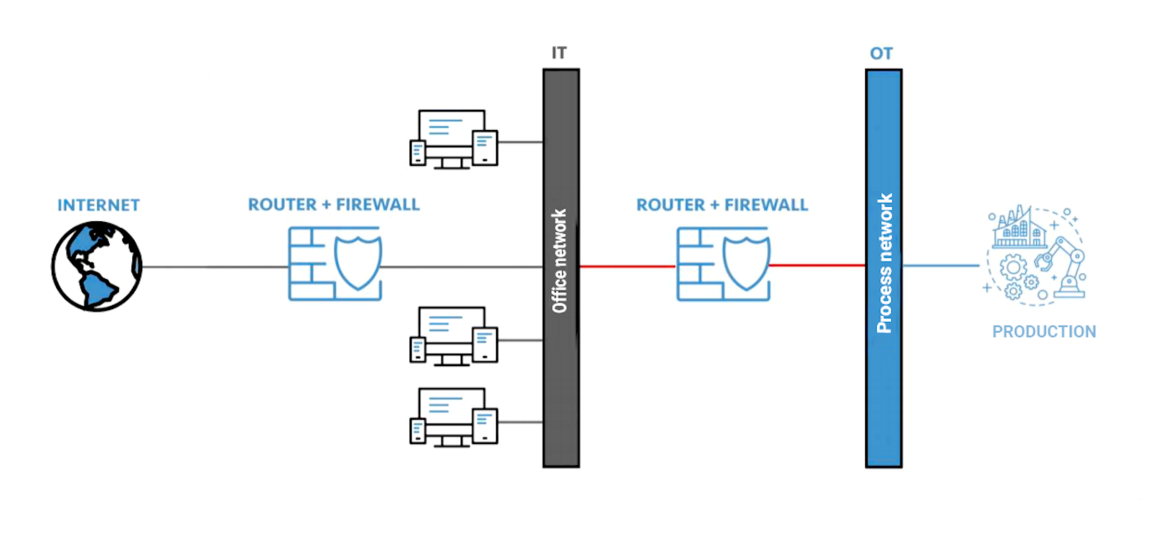
Figure 1. Network Separation by Firewall Source: ARENDAR IT Security GmbH
The pitfall of firewalls is that you can only control which connections you want to allow, but you cannot control the connection itself. Once there is a connection allowed between OT and IT, there is no longer any control of what is sent through this connection. Like choosing a radio station: You can choose which radio station you want to listen to, but you cannot control which song is going to be played next. If a protocol is activated in production to view machine data, in the worst-case scenario the machine can be reprogrammed.
At the same time, it is important to notice that increasing digitalization offers a lot of opportunities for today’s manufacturing companies. With help of predictive maintenance, for example, it is possible not only to collect the machine’s data, but also to visualize it in real-time, so that employees can make the right decisions, and to optimize processes through forward-looking maintenance intervals – just to give one example. This can represent a decisive competitive advantage for the producer.
Bridging the gap but keeping the distance: Implementing an IIoT gateway
What is needed is a mechanism to allow secure communications between the IT and the OT, while keeping control of what passes through the gateway. The Arendar does exactly this. The Arendar is an IoT device for secure data communication between the hermetically sealed production OT (machinery) and the open office IT (classic IT). The separated LAN-Interfaces protect against attacks and hackers. This is comparable to a goods transport. The IIoT (Industrial Internet of Things) gateway loads “goods”, which are in this case production data, and transports them from IT to OT and back again, but the networks themselves are never directly in contact.
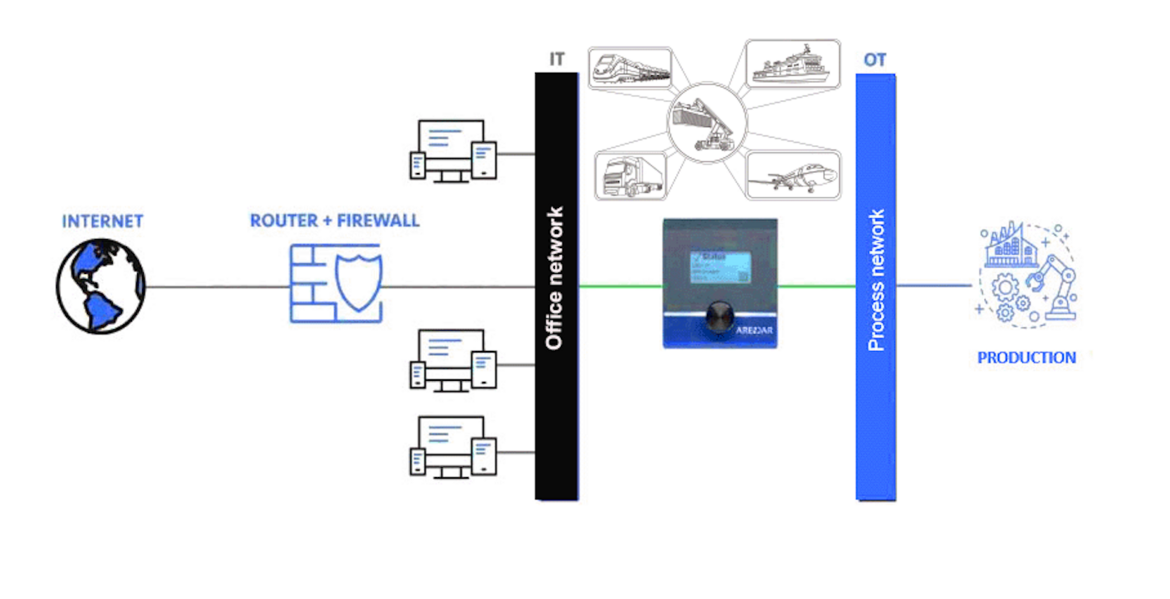
Fig. 2 - Network Separation by Implementation of an IIoT Gateway Source: ARENDAR IT Security GmbH
Additionally, we have found that the businesses we are working with tend initially to hesitate to change their network connection system because they fear the burden. However, the solution is actually very simple. Thanks to different input channels and various connection options, the data acquisition device is highly versatile and adapts to a wide variety of production machines. Hence communication with all components of the production system, the collection of all relevant production data, and M2M communication is possible.
The solution to cyber security is simple
There are three levels of possible modes that the Arendar offers – each with its own level of risk and its own concept of roles and rights. Put simply, this means that data acquisition and control functions can be activated by remote control, while for the remote maintenance functions, physical presence is obligatory. This means if you are given the authority to adapt your technological infrastructure, you still need the operator of the machine to confirm the changes by typing a code on the machine’s control panel.
Every one of us is called upon to be aware of the opportunities and risks of today’s digitalization.
The aim should be to secure critical infrastructure while promoting digitalization. Besides the technical component, there is always a human element influencing cyber security. Be that the machine operator who runs the plant, or the office worker checking emails. Making your employees aware of the opportunities and risks of today’s digitalization and helping them to manage these makes it possible to secure production while still enjoying all the advantages of Industry 4.0. The official website of the US Department of Homeland Security is not the only official site that still names improving password security as the No. 1 Tip for good security habits. Getting this right requires using a password manager and multi-factor authentication, if available. Let us start from here.
Rudolf Preuss began his professional career with a Diploma in Geology from the University of Mainz, in Germany. Following this, he worked as a foreman as an electrical technician, and from 2001 to 2018 he was a self-employed entrepreneur for door automation (Safety and Security). In 2019, he became Product Manager for Arendar at Arend Prozessautomation GmbH, and since July 2019, he has been CEO of ARENDAR IT-Security GmbH.
Please note: The opinions expressed in Industry Insights published by dotmagazine are the author’s own and do not reflect the view of the publisher, eco – Association of the Internet Industry.




