The Current Situation of IoT Security and What to Do
Hardly any IT market sector in recent years has experienced growth rates like those in IoT, but securing networked devices and IoT structures still lags behind, explains Olaf Pursche from the AV-Test Institute.

© EtiAmmos | istockphoto.com
Hardly any IT market sector in recent years has experienced growth rates such as those in connection with networked devices (IoT). As a consequence, it is unavoidable that not only has business with legal IoT boomed, but so has the shadow economy of profit-driven cybercriminals. While respectable product manufacturers and service providers need to raise awareness and build understanding when it comes to customers’ understanding of IT security, criminals can build their business models based on a plethora of poorly-protected or completely unprotected IoT systems. And with the increasing penetration of IoT devices in industrial production, medicine, and additional business fields, as well as consumer households, the threat posed by unsecured IoT devices continues to grow.
IoT malware threats: A doubling of the Linux malware rate
The warnings from the AV-Test Institute in connection with the IoT security situation are anything but new. Our 2016 Security Report already dedicated an entire chapter to this topic. And even four years later, in our new 2020 report, the warning from the IoT lab was unequivocal: “In the race for lucrative market shares, the IoT industry continues to develop multitudes of Internet-connected products without a sufficient security concept and frequently disregarding even absolute minimum standards of IT security.” Hardly anything has changed, however, concerning this trend and the resulting threat scenario.
While there has been little movement in the area of protecting IoT structures since 2016, it is a different story on the attack side. Especially at the beginning of last year, the AV-TEST systems saw exponential growth in malware rates for IoT-typical Linux and Unix versions such as Canonical Ubuntu and others. This trend was already forming at the beginning of 2018 in the detection data of the AV-TEST systems; its growth curve in 2019, however, surpassed even the most pessimistic forecasts. Whereas the analysis of new Linux malware samples for 2018 already indicated a total figure of 188,902 newly-programmed malware samples, the AV-TEST systems in 2019 registered 408,430 new samples, more than double.
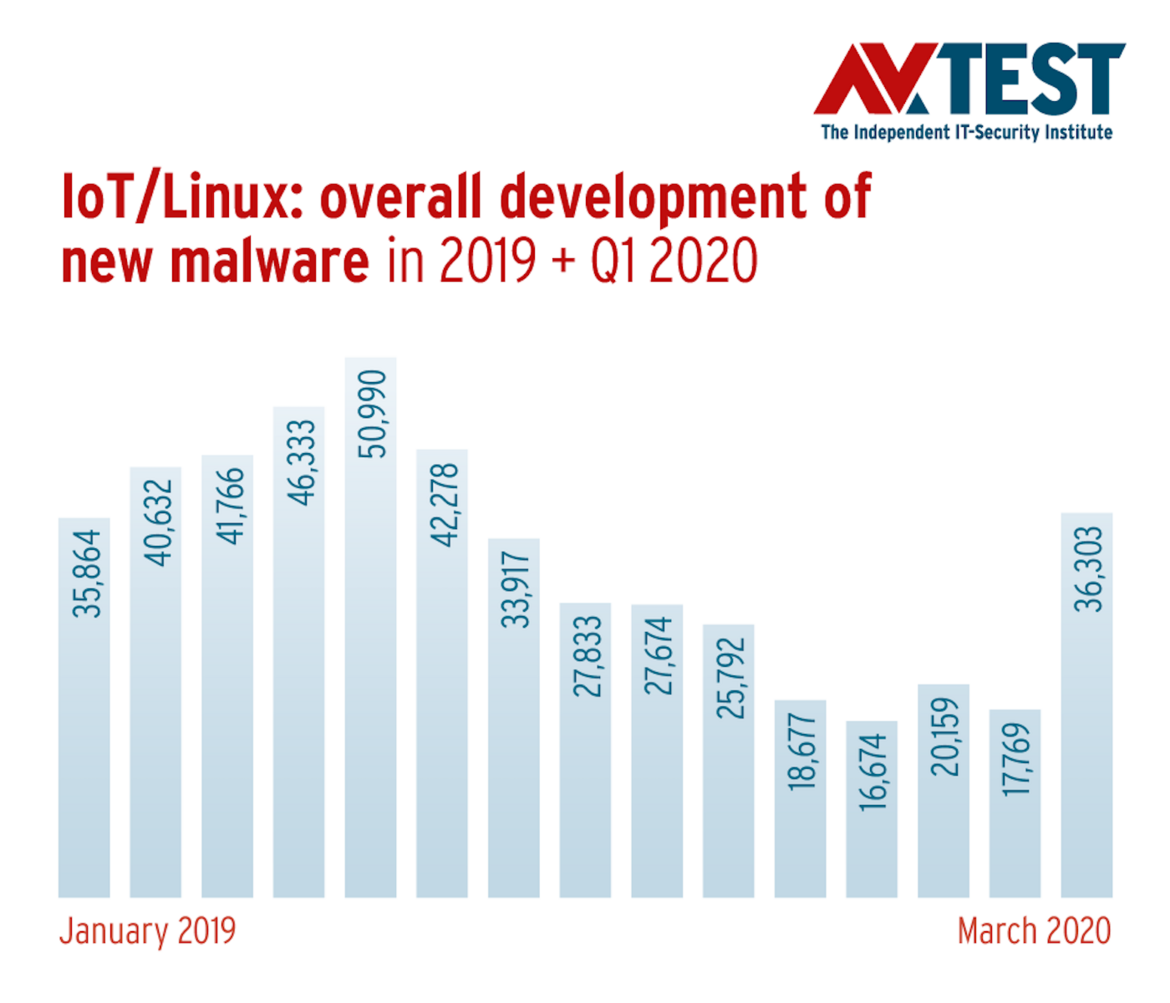
Still no sign that the lessons from the Mirai attacks have been learned
The lion’s share of malware applications for IoT devices on the basis of Linux in 2019 were Trojans, sitting at 41.78 percent. Of little surprise and symptomatic for the unsatisfactory response from IoT manufacturers, even towards well-known threats, several variants of the “Mirai” malware sample continue to rank in the Top 10 of IoT malware, representing a whopping 40.84 percent of overall malware incidence.
The Mirai malware code, originally programmed by kids in September 2016, achieved worldwide attention due to totally haywire distributed denial of service attacks (DDoS) on large online services, including Dyn, Twitter, Spotify, and Amazon, as well as routers of Telekom Deutschland. Given this, surely no manufacturer of IoT devices can claim to not be aware of the threat. Botnets created by the Mirai Trojan continued to proliferate in 2019. New variants of the Mirai malware code work with new tactics and techniques, and are used, for example, to gain control of digital infrastructures in the industrial IoT sector (IIoT). In this way, cybercriminals were able to defeat poorly-protected industrial systems, sabotage them, or exploit their computing power for the mining of digital currency or for the staging of DDoS attacks.
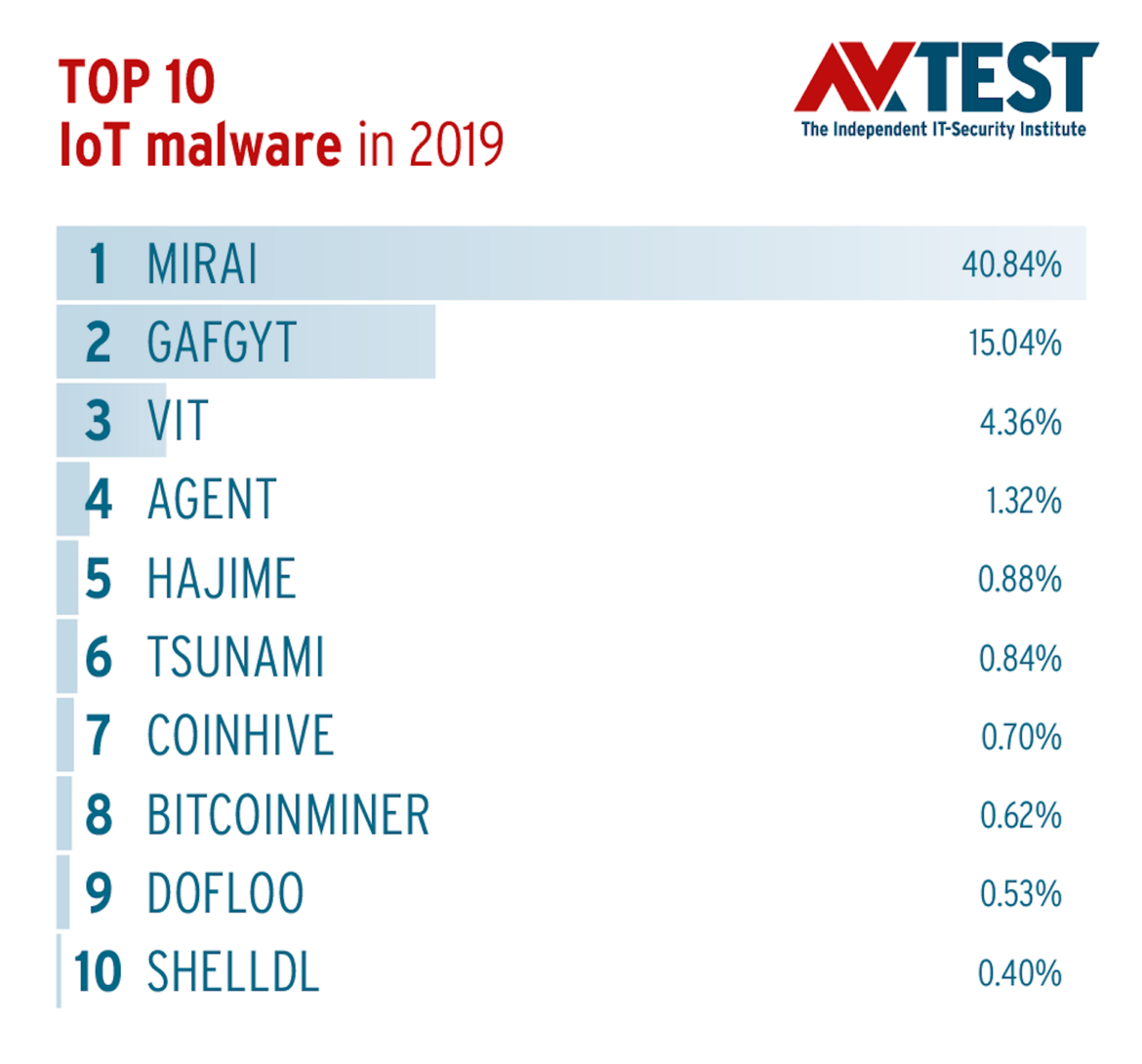
The otherwise virtually unchanged ranking of the most commonly-used IoT malware samples provides a good indication that protection of Internet-based devices is not what it ought to be. Attackers are still able to make a substantial living out of new variants of well-known malware codes. As a result, the same warnings apply today that were already being given by the AV-TEST institute in 2016 reports: Trojans such as Gafgyt (19.04%), Hajime, and Tsunami continue to represent a serious threat to IoT infrastructure.
Crypto miners rely on unprotected IoT infrastructure
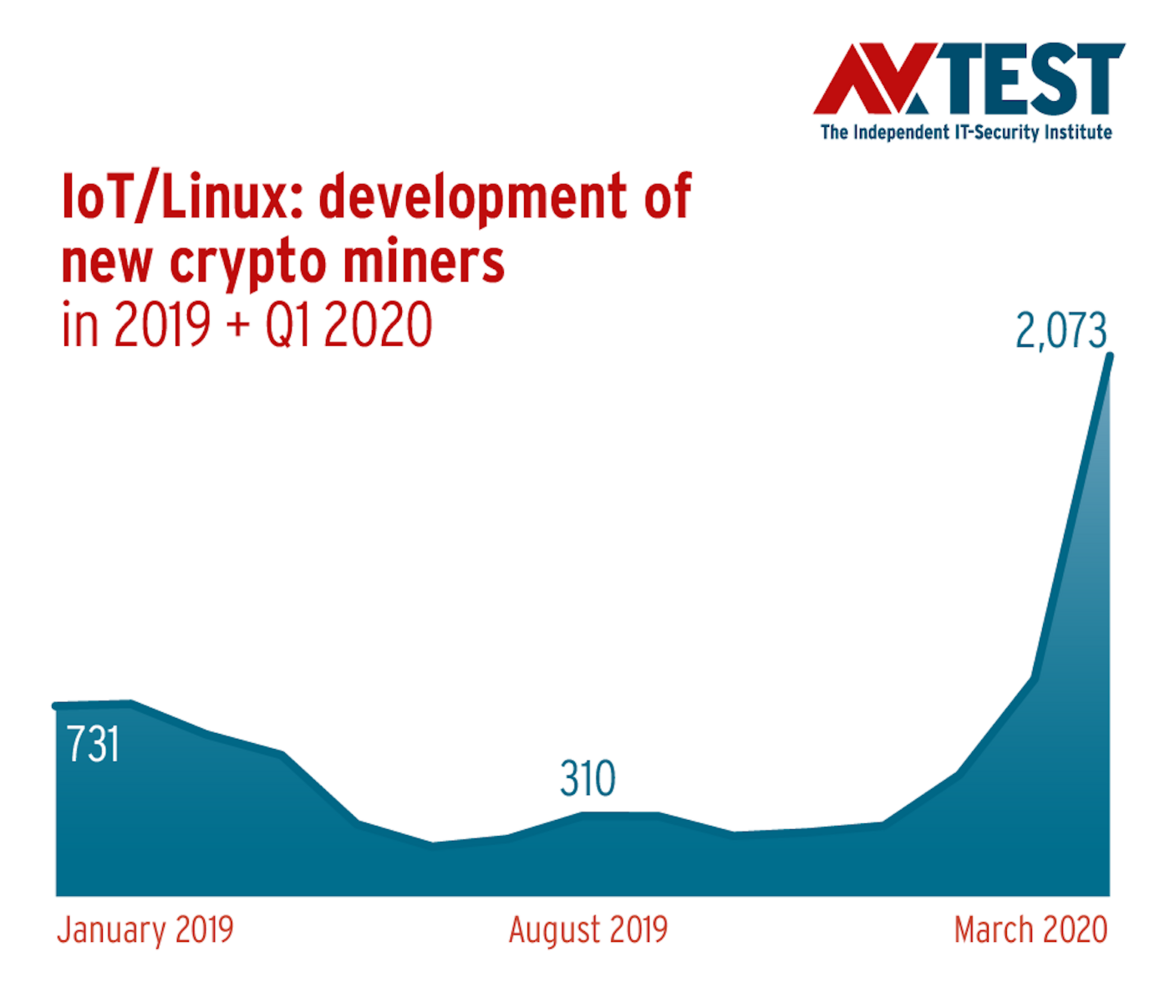
Yet increasingly, malware codes for direct monetization of third-party resources are joining the top ranks of IoT malware. In 2019, for example, two crypto miners already ranked among the Top 10 for IoT.
One of these, Coinhive, is a malware code which at least originally had a semi-legal scope of application. The JavaScript code was originally used for the browser-based calculation of the cryptocurrency Monero and was included by website providers in their online range as a payment option for online services, for example. While the provider of the controversial script shut down its business in March last year, criminals are apparently continuing to use the available Java code to enrich themselves at the expense of unwitting IoT users. AV-TEST discovered a total of 4,697 new samples of this software category in 2019, and thus an increase of 46 percent compared to the previous year’s figures. So there is some evidence that the deployment of third-party resources in the IoT sector is paying off for criminals.
“Business models” used on other platforms, such as digital blackmail through the blocking of devices, are indeed currently being tried out, but thus far they have not become a dominant practice. This is evidenced by the as yet limited penetration of IoT ransomware detected, numbering exactly 56 samples in 2019. But as, in the foreseeable future, IoT devices become increasingly commonplace in industrial manufacturing and medical care, digital extortion rackets through the threat of sabotage of IoT could also become a bitter reality. It would behoove device manufacturers and service providers of both sectors to become aware of this danger and to meet it head on.

IoT security trends in 2020
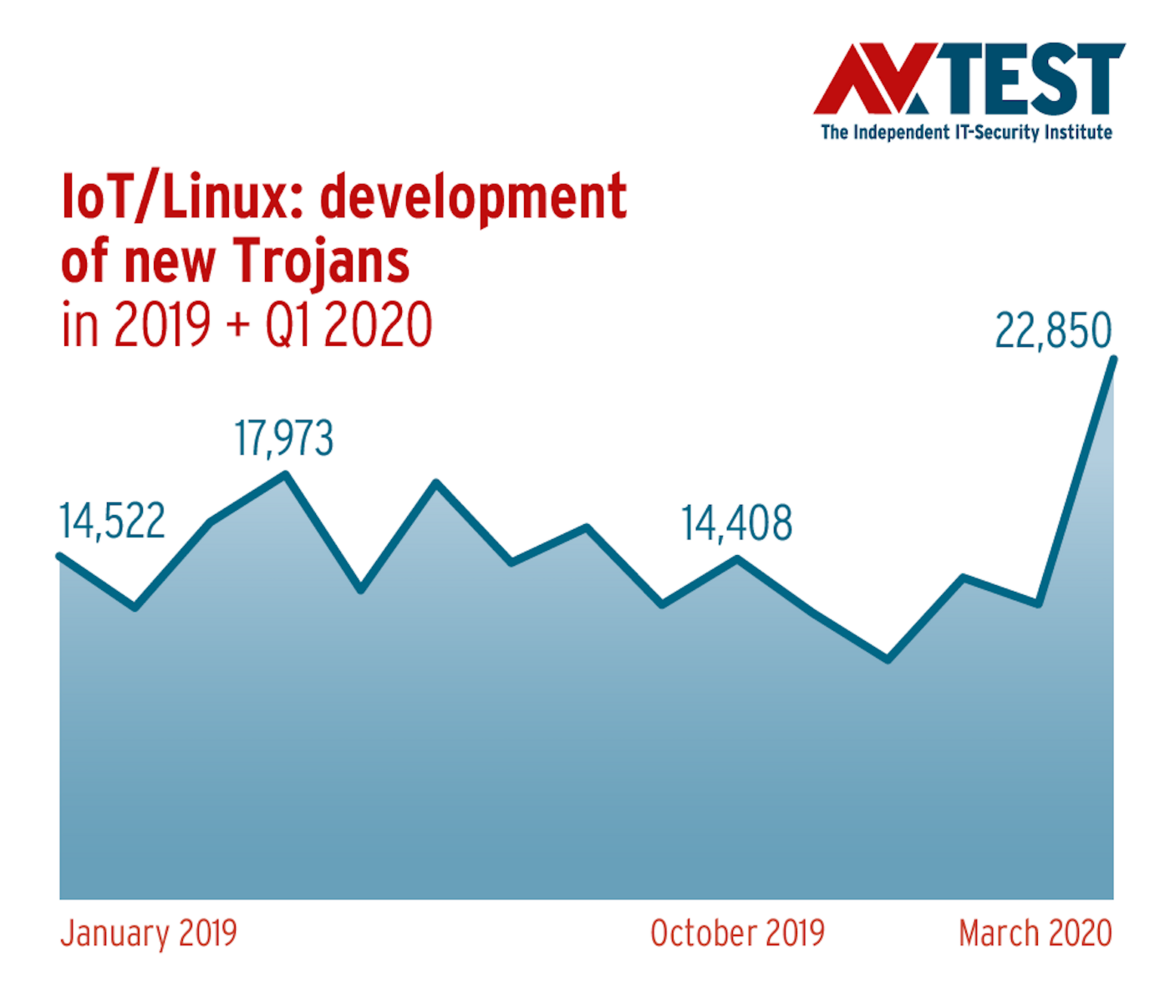
The IoT detection figures of the current year already provide some clues with respect to anticipated malware trends for connected devices. So far in 2020, the rate of Trojans used to infect IoT infrastructure has increased considerably, from just under 40 to over 65 percent. The increase in the rate of newly-developed crypto miners corresponds to the previous analysis. These malware samples have increased their share of overall malware incidence compared to last year from 1.15 to 4.55 percent.
In principle, IoT devices and services offer a wide range of attack vectors: the main targets of criminals are the end devices themselves, connected apps and the mobile devices on which the applications for controlling IoT devices usually run. Nevertheless, IoT devices with inadequate IT security continue to conquer the market. Accordingly, adequate security of IoT devices is becoming increasingly important.
European standardization of IoT security and ETSI EN 303 645
With the European Standard EN 303 645, there is now at least an official minimum requirement for the security of connected devices in the smart home, and a recommendation for the secure development of IoT devices. The standard is based on the previous guideline TS 103 645 and the German security standard DIN SPEC 27072, which was co-developed by the German Federal Office for Information Security (BSI) and has also been included in the creation of the new European standard.
AV-TEST has been calling for the development described in the EN 303 645 standard for years and has never tired of advising the BSI in the expert council IT-Security. AV-TEST therefore welcomes the current measure. It corresponds to a necessary minimum standard for IoT security, which all devices certified by AV-TEST have long since fulfilled and regularly prove in extensive tests.

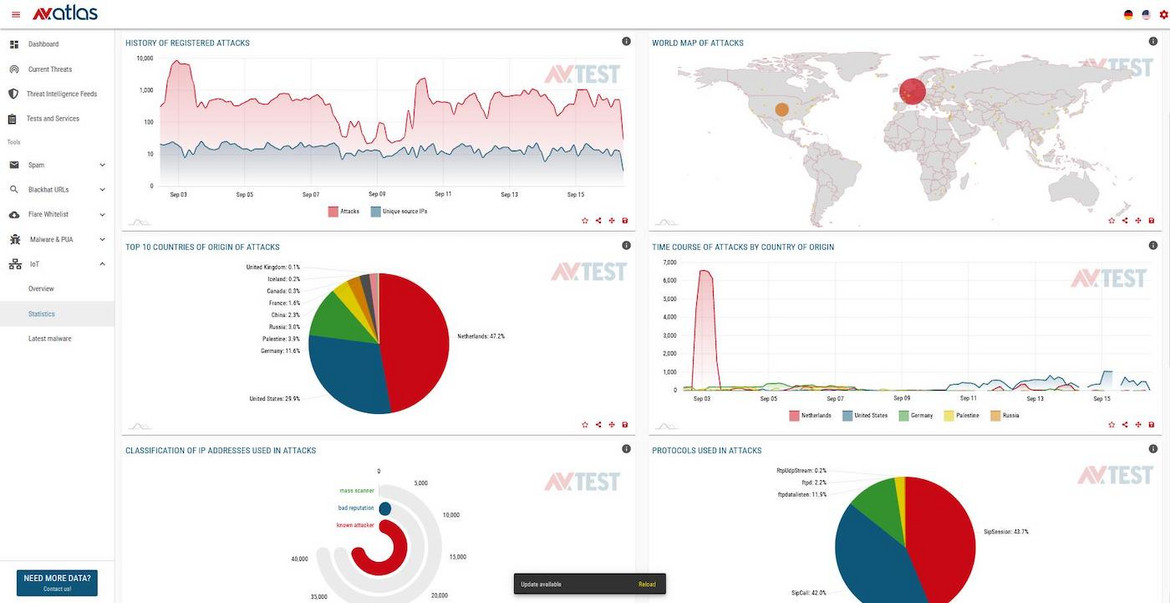
AV-ATLAS supports suppliers with real-time data on IoT attacks
To provide both product manufacturers and their customers with constantly updated data on the threat situation in IoT, AV-TEST this year launched the IoT section in the AV-ATLAS Threat Intelligence Platform (av-atlas.org). We now offer real-time threat analyses of virtually all relevant IoT platforms, to guide users and to support manufacturers. The website, available free of charge, offers a query capability both for information on past and current attacks, along with the malware deployed and its precise analysis. The AV-TEST Institute will complement the extensive data spectrum of its AV-ATLAS Threat Intelligence with real-time monitoring data of IoT devices and services.
The data gathering is based on four different HoneyPot systems, which cover the widest possible range of IoT systems that are currently in use. The new analysis system not only provides information about the origin and timing of IoT attacks; it also reports on the IP addresses used in outbound attacks, the login data used, the commands executed during attack attempts, and any uploaded files. Supplemented by the AV-TEST Institute’s tried-and-tested analysis systems, the new system also identifies the malware used in attacks. AV-TEST Institute offers this data and information to product manufacturers and service providers in order to secure and optimize their products.
Also as a member of the IoT Advisory Board of the eco Association, the AV-TEST Institute will continue to promote security and privacy of IoT products. Alongside the growing number of European manufacturers who gain a competitive advantage by having the security and privacy of their products tested and certified by AV-TEST, the number of end-customers who increasingly value certified security and use it as an argument in their product decision making is also growing.
IoT devices and services that, by design, demonstrably and credibly take their customers’ security and data protection into account, instead of just respecting the undoubtedly required minimum level of security, are the more sustainable and trustworthy products and will ultimately prevail with customers. We at AV-TEST are one hundred percent convinced of this. And with every future security and data breach, users will find that every cent they spent on security and data protection was well spent. After all, IoT products can already be found in almost all areas of our lives, whether at home or in the office. And in an increasingly digitalized world, with all its advantages and disadvantages, the old adage certainly applies: Trust in digital security is good, verified and proven security is better.
Olaf Pursche is CCO of the AV-TEST Institute in Magdeburg, Germany. In early 1990s, he worked at the Institute of Law and Informatics of the Leibniz University of Hanover, was PC Professionell Magazine‘s editor for Computer & Law topics and tested Security Software and Internet Services. He developed the IT Security editorial and testing division of Europe‘s largest computer magazine, COMPUTER BILD, which he headed for 15 years and wrote for several newspapers. Since 2015, he is responsible for Communications, Press Relations and heads the Marketing Department of the AV-TEST Institute. He is a member of the advisory boards of public authorities like the Expert Council Cyber Security of the German Federal Office for Information Security (BSI), the advisory board IoT of the ECO association and the Competence Group Security, consultant in the expert group IoT of the Association of German Insurers (GDV) and other trade organizations.
Please note: The opinions expressed in Industry Insights published by dotmagazine are the author’s own and do not reflect the view of the publisher, eco – Association of the Internet Industry.




